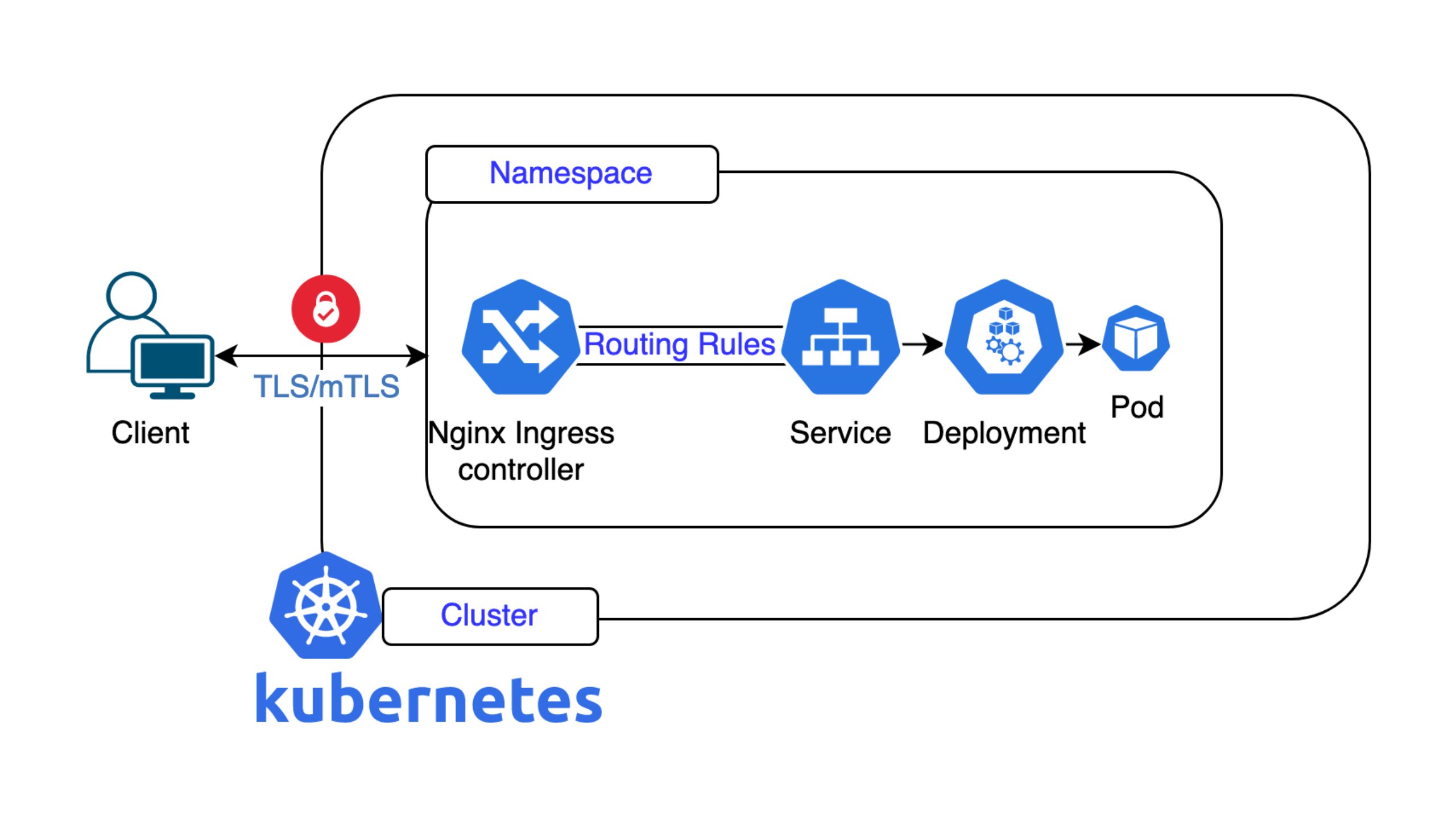
In the digital world, server security is not a “nice-to-have” but one of the cornerstones of a smooth operation. As a customer of a managed service provider, you trust that your infrastructure is robust and protected. But what does “secure” actually mean in practice?
Perhaps you have already run a security scan on your application and received a report listing potential vulnerabilities. These reports are valuable, but without the right context, they can also cause uncertainty.
Today, we would like to show you the basic measures we take to ensure the security of your servers and why many automated alerts are often false positives.
The Heart of Security: A Well-Thought-Out Patching Philosophy
Perhaps the most important aspect that allows you to assume general security is our approach to software updates. We use Ubuntu LTS versions for your server operating systems, which are released every two years. The addition of LTS in the name reveals that these are versions with long-term support. Instead of immediately jumping to the next higher version of a software (such as OpenSSH) every time a security vulnerability is discovered, Canonical, the manufacturer of Ubuntu, actively ports the necessary security patches back to the stable LTS versions (“backporting”). This prevents breaking changes from being incorporated into the software that could interfere with productive operation. Unfortunately, however, simplistic scans often cause unnecessary uncertainty.
What Does That Mean for You?
A security scanner may detect a software version that appears outdated at first glance (e.g. OpenSSH 8.2p1) and report it as vulnerable. In reality, however, this version is fully protected against the reported vulnerabilities by the backports we have installed. The version number alone is not meaningful here; the actual patch level is what counts.
Secure Configuration Is A Must
In addition to patching, the configuration of services is crucial. We take care to provide a secure and sensible configuration from the outset.
- TLS/SSL encryption: We configure web servers to offer broad compatibility with various clients (browsers, etc.) without compromising security. Our engineers follow the recommendations of the Mozilla Foundation, which represent a good compromise between security and compatibility and lead to good ratings in common tests such as the Qualys SSL Check.
- Dealing with SSH: The OpenSSH service is a frequent target of attacks. The software is considered extremely secure and is managed by us accordingly. Many CVEs (security vulnerabilities) reported in reports are often false positives in practice, as they have already been fixed, are classified as controversial bugs by developers, or affect functions that we do not use at all (e.g. the FIDO authentication mechanism). Simply checking the SSH version number is not enough.
Reminder:
The version displayed during connection establishment does not indicate the patch level of the service.
- Useful default settings (default vhost): We configure “default vhosts” (standard websites). These prevent search engines from accidentally indexing customer content under the server’s pure IP address. The use of self-signed certificates for these default vhosts is also a conscious technical decision to avoid error messages if no customer certificate has been installed yet – even if scanners sometimes report this as a “problem”.
The following always applies: We respond to your individual wishes and take into account configurations with regard to greater compatibility or greater security.
Consulting, Not Just Administration
Providing sound advice is important to us. We are happy to assist you with any questions you may have about the security of our infrastructure. Our documentation also includes a practical guide on how to deal with the results of a security scan: “Interpreting a security report for your server”.
Multi-Layered Security for Fundamentally Secure Servers
The security of your servers here with us is based on a multi-layered approach: a robust patching strategy that goes beyond mere version numbers, a secure basic configuration of essential services, and transparent consulting that helps you avoid insecure protocols.
So the next time you analyze a security report, you can rest assured that many of the issues reported have most likely already been addressed by our in-depth management processes or can be classified as false positives.