The first TechTalkThursday in 2025 – and number 23 of the event series – took place on the 6th of March 2025 at 6PM in our office. We were very pleased to welcome two external speakers and one 9er who all gave captivating speeches. There were around 30 people attending the event, some of them Nine employees, some speakers’ guests and many external attendees interested in the topics of autonomous coding agents, SCION – a new internet architecture – and live migration for containers on Kubernetes.
This TechTalkThursday was again live-streamed on YouTube and we were happy to welcome some listeners also on that platform. As usual, Thomas Hug, the founder and CEO of Nine, kicked off the event with a short introduction, presenting the speakers and their upcoming talks. The three speakers were Silvan Mühlemann, CTO & co-founder of mühlemann+popp, Samuel Hitz, CTO at Anapaya Systems, and Cyrill Troxler, Senior Engineer Platform at Nine.
From Prompt to Production: Developing and Deploying Applications with Autonomous Coding Agents
In his engaging talk, Silvan Mühlemann, CTO of mühlemann+popp, a software agency based in Zurich, shared his hands-on experiences with autonomous coding agents, particularly highlighting the tool Cline used in combination with Mac Whisper for voice-driven programming. Demonstrating how he codes while biking using voice commands, Silvan underscored the productivity boost these tools offer, reducing what once took weeks to mere minutes.
He showcased a live demo where Cline builds a front-end seat reservation app for our TechTalkThursday – if we ever were to introduce such a thing. Despite occasional unpredictability in agent behavior, Silvan noted the agents’ ability to perform self-testing and deploy applications autonomously using tools like Deployer and Firecrawl. He emphasized the importance of guiding the agents with clear instructions and intervening when necessary, especially for deployment or version control tasks.
Silvan also reflected on real-world applications he developed using agentic tools – including a quiz generator, subtitle editor, and LLM performance tester – stressing their effectiveness for small, backend-heavy tasks in familiar tech stacks like Python and TypeScript. However, he cautioned against relying on them for aesthetic frontend work or large-scale production codebases, citing their current limitations in contextual understanding and creative visual design.
His key takeaways included that it makes sense to use coding agents for tasks within your domain knowledge, employ strategies like a «memory bank» to improve context retention and to keep files concise – i.e. under 250 lines – and validate outputs. Silvan also mentioned the importance of generating unit tests to ensure reliability and treating agentic tools as collaborative partners that require oversight.
He concluded his talk with the statement that while these agents are not flawless and require user familiarity and intervention, they represent a significant leap in developer productivity. He’s optimistic about their evolution and envisioned a future where engineers delegate mundane coding tasks entirely to such tools.
Scalability, Control, and Isolation on Next-Generation Networks (SCION): a New Internet Architecture
Then, it was Samuel’s turn. The CTO of Anapaya introduced SCION – Scalability, Control, and Isolation On Next-generation networks –, a new internet architecture designed to address the fundamental shortcomings of today’s internet, particularly for critical infrastructure like finance, healthcare, and energy.
In his speech, Sam argued the internet’s design, while historically successful, lacks control, transparency, and security. Once data enters the internet, its path is uncontrolled, potentially violating privacy laws or jurisdictional boundaries. SCION aims to solve this through three core principles:
- Path Control – Unlike traditional routing where data paths are unpredictable, SCION allows data senders to choose from a set of verified network paths. This enables geofencing, jurisdictional compliance, and performance tuning (e.g., choosing low-latency paths for video or high-throughput ones for backups).
- Isolation Domains (ISDs) – They group networks under a shared trust anchor and governance. Countries or sectors (like banking) can form ISDs, enhancing sovereignty and trust. Path control is enforced at the network level, not just via firewalls.
- Cryptographic Security – Both control and data planes are cryptographically protected. Routers use efficient symmetric cryptography (e.g., AES) for packet verification, enabling high throughput without complex hardware.
Samuel mentioned that SCION is already in production. Anapaya’s technology supports it through core network routers («Core») and tunneling gateways («Edge») that encapsulate standard IP traffic. This means applications require no modification to use SCION, making adoption practical. A key use case is the Secure Swiss Finance Network, connecting 100+ banks securely and flexibly without relying on centralized infrastructure. The system ensures that only certified entities can join, enforcing access via certificates tied to ISDs.
Sam also highlighted SCION’s real-time traffic engineering capabilities through a visual console. Users can monitor, simulate, and control traffic based on sensitivity and policy, achieving fast failovers and optimized routing across multiple ISPs and jurisdictions. Samuel stated that in essence, SCION represents a significant leap forward in secure, sovereign, and programmable networking tailored for the demands of the modern digital world.
Exploring Live Migration for Containers on Kubernetes
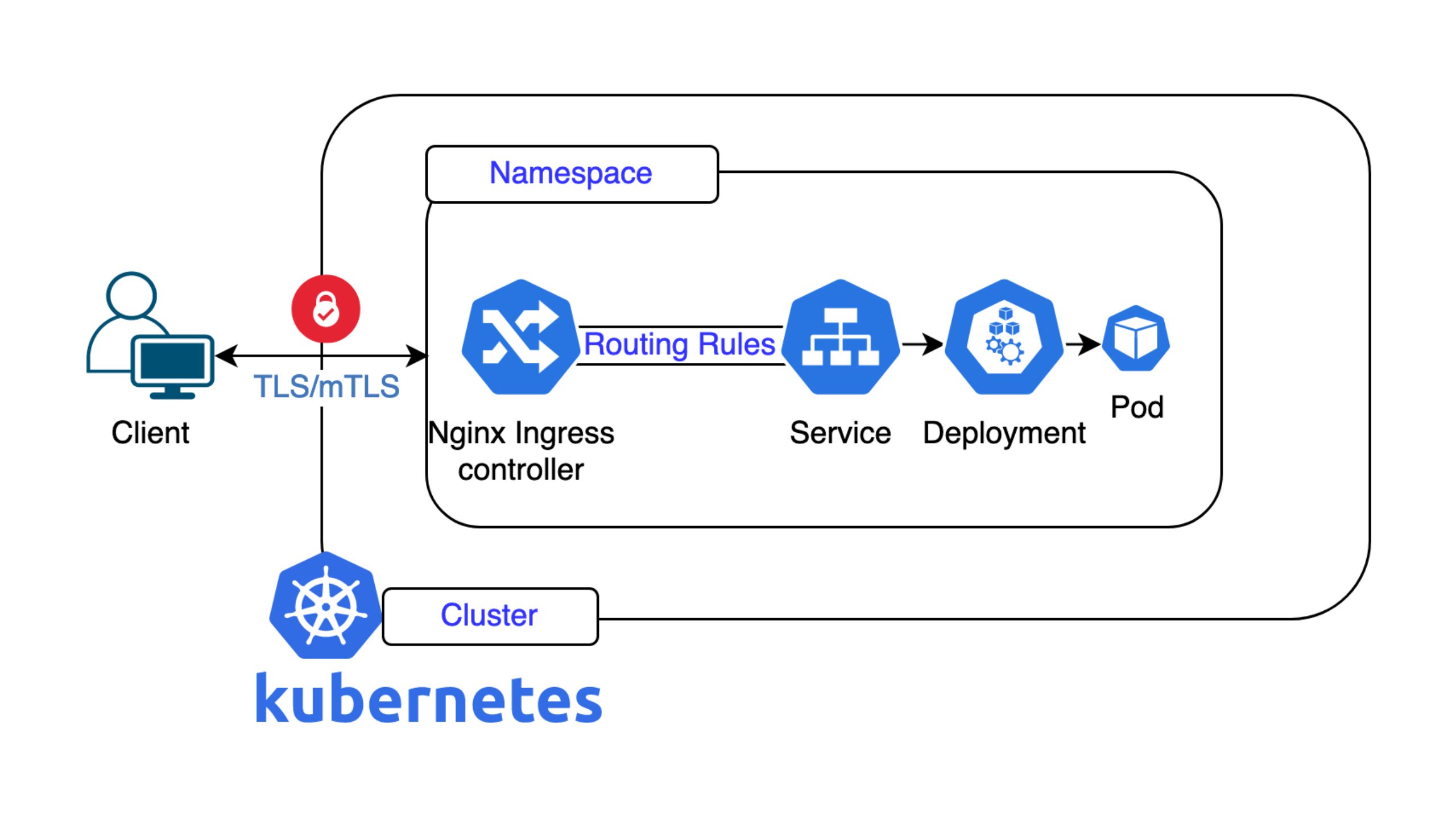
Last but not least, it was Cyrill’s turn. Our senior platform engineer introduced Zeropod, a new container runtime for Kubernetes designed to optimize resource usage through container snapshotting and fast recovery. Zeropod snapshots idle containers to disk and restores them in sub-second time upon demand. Cyrill said that this is particularly effective for workloads where many containers are infrequently accessed.
He then explored a key challenge: node failure or scaling down can disrupt these frozen containers. His solution is container migration using pre-existing snapshots. During node drain events, containers are automatically restored on another node using saved state, ensuring continuity and saving costs by avoiding unnecessary autoscaling.
The talk also included a demo of both offline migration (for paused containers) and live migration (for running containers). Live migration mimics techniques used in VM migrations like pre-copy and post-copy. Zeropod uses CRIU (Checkpoint/Restore In Userspace) to support iterative and lazy migrations. In lazy migration, only minimal state is transferred initially; full memory pages are fetched on-demand using Linux’s userfaultfd mechanism, minimizing downtime (typically ~200ms).
Cyrill highlighted Zeropod’s practical integration: it works via a Kubernetes runtime class and requires minimal setup. It supports stateless applications well, but has the following limitations:
- No support yet for ephemeral storage or StatefulSets
- Live migration is limited to single-container pods
- Kernel support (userfaultfd) is required, which isn’t available on all distros (e.g., Flatcar).
He stated that security is ensured by tunneling memory pages through encrypted MTLS channels. The project remains experimental, with features like live migration planned as optional in future releases. Cyrill’s work on this topic represented a promising step toward more flexible, resilient, and resource-efficient Kubernetes workloads, especially in edge computing or highly dynamic environments.
Want to Stay Up to Date?
Subscribe to our YouTube channel and regularly visit our website’s blog.